Pennsylvania CTE School Embeds UDL to Reach More Learners, Upskill Teachers
Faced with a uniquely diverse student body and a staff drawn largely from industry, UBCTS has overhauled how it supports teaching and learning by adopting Universal Design for Learning (UDL) across its career and technical education (CTE) programs. The school partnered with CAST—the nonprofit that pioneered UDL—to train educators, build a common instructional language, and […]
Read MoreBattle of the AIs: An Educator’s Guide to Choosing the Right AI Platform
Choosing an AI platform for school operations is no longer a matter of personal preference; it’s a governance decision that affects cost, workflow, security, and public trust. While many tools appear similar at first glance, especially at the free tier, the features districts truly need—administrative controls, identity management, usage reporting, reliable integrations, and content safeguards—live […]
Read MoreIs React Native Good for Mobile App Development? Cost, Speed & Scalability
React Native is one of the most debated choices in mobile development. Some teams swear by its rapid iteration and cross-platform velocity; others insist you can only achieve a truly premium mobile experience with fully native stacks. The truth is more nuanced. In 2025, React Native remains a strong, production-ready framework backed by a massive […]
Read MoreHow To Generate Leads For Mobile App Development: Proven Strategies That Work
Winning quality leads for mobile app development isn’t about one silver-bullet tactic. It’s the compounding effect of positioning, content, outreach, partnerships, and a disciplined sales process—executed consistently. This long-form, step-by-step playbook distills what high-performing studios and solo founders do to attract, qualify, and close buyers in competitive markets. You’ll get concrete frameworks, copy templates, channel […]
Read MoreWhat Is Cross-Platform App Development? Frameworks, Pros & Use Cases
Cross-platform app development is the practice of building a single application codebase that can target more than one platform—typically iOS and Android, often the web and desktop too. Instead of staffing separate teams and writing the same features twice, you architect once, ship everywhere, and maintain in one place. The promise is faster time to […]
Read MoreApple preps enterprises for AI era with new controls for ChatGPT—and any “external” provider
Apple is adding a new layer of enterprise controls to its fall software releases that will let IT teams decide if—and how—employees can use ChatGPT and other “external” AI services from Apple devices. The change, arriving alongside iOS 18, iPadOS 18, macOS Sequoia and more in September, gives organizations granular switches to route, restrict, or […]
Read MoreBluesky goes dark in Mississippi rather than comply with sweeping age-verification law
Jackson, Miss. — Bluesky, the decentralized social network, has blocked access to its app and website for people connecting from Mississippi after the state’s new age-assurance law took effect. The company said the statute would force it to verify the age of every user—collecting and storing sensitive data and obtaining parental consent for anyone under […]
Read MoreApple.com: Navigate, Compare, Decide
Apple’s best tools, answers, and offers live at apple .com—the central hub for everything: product pages for iPhone, iPad, Mac, and Apple Watch; the online Apple Store; Apple Support; step-by-step how-tos; and account controls for Apple ID, iCloud, and subscriptions. Whether you’re new or seasoned, apple .com minimizes friction so you can pick the right […]
Read MoreWalmart.com: Mega Deals, Fast Delivery & Everyday Savings
Walmart .com is the doorway to one of the world’s biggest retailers—more than a cart and a “Place order” button. It unites national brands, Walmart private labels, and a vast marketplace with rapid delivery, curbside pickup, and Walmart+. In short, walmart .com pairs everyday low prices with logistics so routine purchases become quick, repeatable, and […]
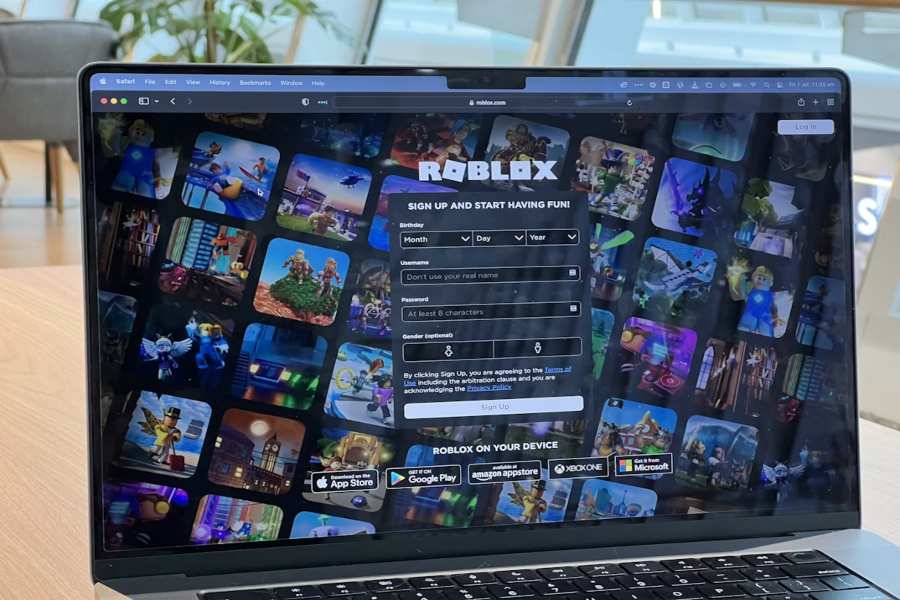
Read MoreRoblox.com: Start, Play, Create, and Stay Safe
The official roblox .com website is the front door to one of the world’s most active gaming platforms and creator ecosystems. Through roblox .com, you create an account, manage your avatar, discover experiences, buy and monitor Robux, adjust privacy and security, and launch the app on your preferred device. Millions of user-generated games—“experiences”—are updated daily, […]
Read More